Protecting your network isn’t the same for everyone.
Get Tested for your own unique vulnerabilities.
Our Risk-Based Penetration Testing process is a comprehensive cybersecurity assessment that focuses on implementing threat actor TTPs to emulate the real-world risk within an organization’s environment.
Risk- based testing helps organizations proactively identify and address weaknesses in their defenses, ultimately providing a more realistic and comprehensive assessment of the security resilience against sophisticated, real-world cyber threats. The emphasis on likely attack paths and adversary behavior enables organizations to prioritize and allocate resources more effectively to enhance their overall security posture.
This comprehensive view will provide immediately actionable results, allowing organizations to quickly identify, remediate, and prevent the attack paths that adversaries are exploiting.
Key Features
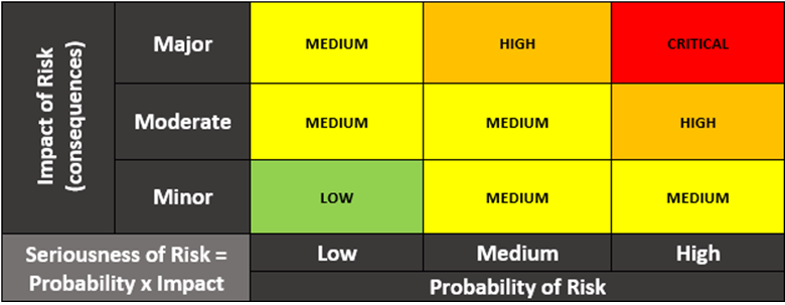
Risk Prioritization
Risk-Based Penetration Testing evaluates and ranks potential threats based on their potential impact on the organization and the likelihood of their occurrence. This allows for a more targeted approach, ensuring the most critical exposures are addressed first.
Dynamic Threat Monitoring
This test incorporates evolving threat landscapes by continuously updating risk profiles, ensuring that the test remains relevant to current threats and vulnerabilities.
Realistic Threat Assessment
By emulating the tactics, techniques, and procedures (TTPs) of actual threat actors, risk-based testing provides a realistic scenario for evaluating security measures. This helps to enhance the overall security posture against all of the most likely threats you’ll encounter.
Customized Scenarios
Risk-Based Penetration Testing creates realistic attack scenarios tailored to the organization’s industry, size, technology stack, and business model. This ensures the test is as realistic as possible.
Securing Your Wireless Network… How It’s Done
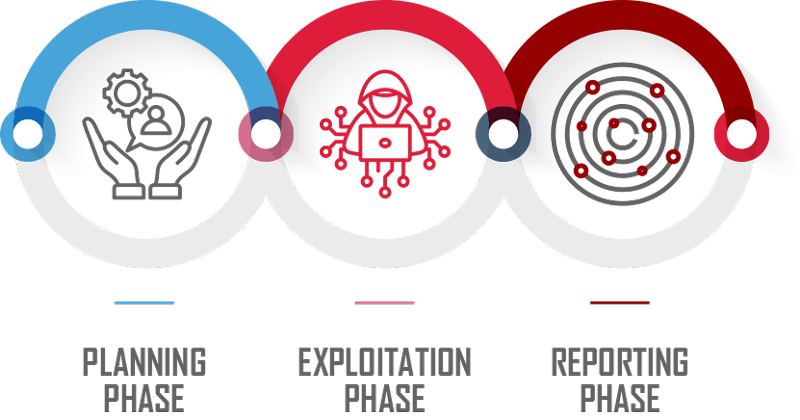
Our team of Security Engineers follow a set of proprietary evolving methodologies, divided into three phases, to traverse your wireless network’s vulnerabilities just like a bad-actor would. We then provide a detailed report to aid in the effective remediation of all security gaps.

